Simple Ways to Stay Safe Online (Even If You’re Not Tech-Savvy)

Staying safe online has never been more important. From shopping and banking to social media and remote work, much of our lives now exist on the internet — making cybersecurity awareness essential. Whether you’re a casual browser or spend most of your day online, learning how to protect your data can save you from identity theft, scams, and privacy breaches.
This guide breaks down practical, easy-to-follow tips to keep your digital presence secure, no matter where or how you connect.
Think Before You Share Anything Online
Social media platforms like Facebook and other social networking sites make it easy to stay connected. But oversharing can put your privacy — and even your safety — at risk.
Before posting or uploading content, ask yourself: Would I be okay if this were public? Even if your account settings are private, screenshots and leaks can expose your posts. Remember, once something is online, it’s nearly impossible to erase completely.
Avoid sharing:
Personal information like your address, school, or workplace
Photos that reveal location data (geo-tags)
Sensitive opinions or content that might embarrass you later
Pro Tip: When unsure, don’t post. It’s better to stay cautious than regretful.
Don’t Believe Everything You Read on the Internet
The internet is an incredible resource for information — but it’s also home to misinformation, scams, and clickbait. Anyone can create a website, and not all content is trustworthy.
Watch out for:
Websites spreading false news or exaggerated claims
Fake health or investment advice
Download links that may contain malware
To stay safe:
Check the credibility of the source
Look for professional design and correct grammar
Verify facts using multiple reliable websites
Use Strong, Unique Passwords for Every Account
One of the easiest ways to protect your online accounts is by using strong, unique passwords. Avoid predictable combinations like “123456” or “password.”
How to Create Secure Passwords
Combine upper and lowercase letters, numbers, and symbols
Use a phrase instead of a single word
Avoid personal details like your birthday or pet’s name
Consider using a password manager to store and generate secure passwords for each site you use.
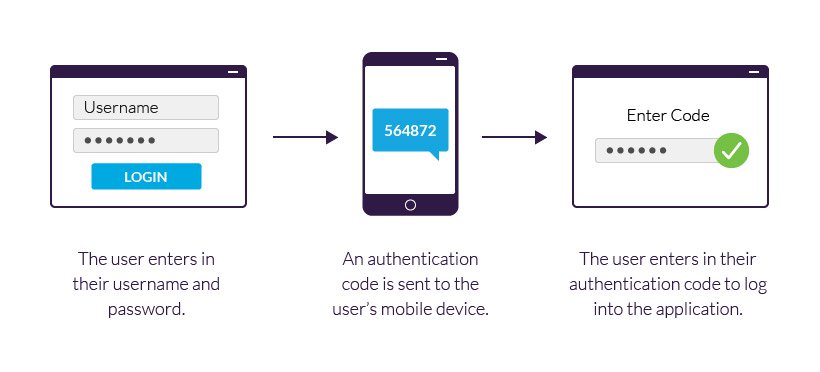
Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of protection by requiring both your password and a verification code sent to your phone or email. Even if hackers steal your password, they can’t access your account without this code.
Most major platforms like Google, Facebook, and Apple support 2FA. It takes just a few minutes to set up — but provides long-term peace of mind.
Keep Your System and Software Updated
Software updates often include security patches that protect your device from new threats. Using outdated software can leave you vulnerable to attacks.
Tips for staying updated:
Turn on automatic updates for your operating system
Regularly check for browser and app updates
Avoid using unsupported operating systems like Windows XP
Keeping your system up to date helps prevent hackers from exploiting known vulnerabilities.
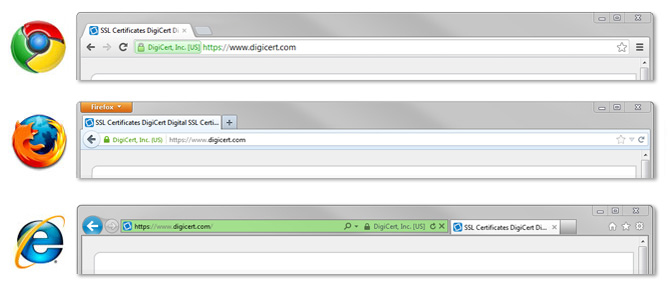
Always Check if a Website Is Secure
Before entering sensitive information, make sure the website uses HTTPS encryption.
Look for:
A small lock icon beside the URL in your browser
A URL that begins with https:// instead of http://
If a site doesn’t have these indicators, it may not be safe for online transactions or personal data entry.
Be Aware of Phishing Scams
Phishing scams are designed to trick you into revealing login credentials or financial details. These attacks often come through fake emails or websites that look legitimate — for example, pretending to be your bank or an online store like Amazon.
Signs of a phishing attempt:
Urgent messages asking for immediate action
Suspicious links or misspelled domains
Attachments from unknown senders
If you’re unsure, go directly to the official website instead of clicking links in emails.
(Learn more about online scam prevention in our related guide on how to protect yourself from phishing attacks.)
Be Careful with Email Attachments and Links
Email remains one of the most common ways for hackers to spread viruses and malware. Never open attachments or click on links in emails from unknown senders — even if they appear to come from someone you trust.
Best practices:
Scan attachments with antivirus software before opening
Avoid downloading unsolicited files
Verify with the sender through another channel if in doubt
Read Before You Accept or Install Anything
Pop-up prompts asking you to install programs, browser extensions, or updates may sometimes contain hidden software. Always read terms and permissions before clicking “OK” or “Install.”
Watch for checkboxes that allow third-party toolbars or add-ons — these often cause performance issues or invade your privacy. If the installation isn’t essential, cancel or close the window.
Be Mindful When Using Shared or Public Computers
Logging into personal accounts on work or public computers can be risky. Employers or administrators may have monitoring tools or keyloggers installed to track user activity.
If you must sign in:
Avoid saving passwords in the browser
Log out completely when finished
Use private or incognito mode
At a friend’s house or in a shared environment, the same rules apply — never store login credentials on a computer that isn’t yours.
Choose a Secure, Modern Web Browser
Outdated browsers like Internet Explorer no longer receive security updates, leaving users exposed to online threats. Modern browsers like Google Chrome, Mozilla Firefox, or Microsoft Edge offer better protection and frequent updates.
Modern browsers also include built-in phishing protection and sandboxing technology to keep your system secure.
Keep Browser Plugins and Extensions Updated
Attackers often exploit outdated plugins such as Adobe Flash or Java to gain access to systems. Regularly check your browser’s extensions and remove any that you no longer use.
Make it a habit to:
Update plugins manually or enable auto-updates
Download extensions only from trusted sources
Avoid plugins that request unnecessary permissions
Store Your Passwords Securely
Avoid writing your passwords on paper, sticky notes, or unencrypted files. Instead, use trusted password management tools or encrypted storage solutions.
Password managers not only secure your credentials but also generate strong passwords for new accounts — reducing the risk of repeated or weak logins.
Protect Your Computer from Malware and Viruses
Install reputable antivirus software to safeguard your device. Programs like Windows Defender come pre-installed on newer Windows versions and offer reliable real-time protection.
You can also add anti-malware programs such as Malwarebytes to detect additional threats like spyware or adware.
Additional protection tips:
Schedule regular virus scans
Avoid downloading pirated software
Be cautious of free online tools that require installations
Verify Downloads Using Checksums
When downloading software, check if the site provides a file checksum (like SHA-1 or MD5). A checksum allows you to verify that the file hasn’t been altered or corrupted during download.
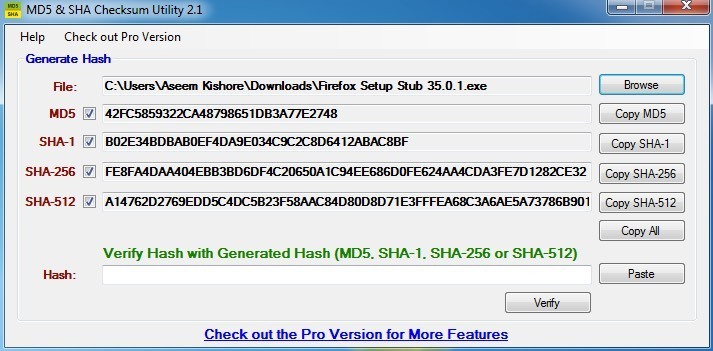
To learn how, read this step-by-step guide to verifying installer checksums.
Final Thoughts: Stay Alert and Stay Informed
Online safety isn’t about paranoia — it’s about prevention and awareness. By taking small steps like updating your software, using strong passwords, and avoiding suspicious links, you significantly reduce your risk of being hacked or scammed.
The internet will always evolve, but so can your habits. Keep learning, stay cautious, and you’ll enjoy a safer, more secure online experience.
Related Posts

Tue, Mar 20, 2018 12:18 AM
Broadband Deals Money SubscriptionHow Much Are You Really Paying Per Minute for Your Streaming Services
Streaming isn’t cheap anymore — but how much are you really paying per minute of Netflix, Disney+, or Spotify? We crunched the numbers so you can see which subscriptions give you the best bang for your buck.
Tue, Mar 20, 2018 12:44 AM
Technology Broadband InstallationInternet Provider Installation FAQs
Guide to Internet Provider Installation

Fri, Jul 6, 2018 7:04 PM
Eco-FriendlyWhere to recycle your technology hardware!
Easy tips on recycling your old computers and phones

Fri, Dec 6, 2019 4:22 PM
SafetyAlways Check the Website You Visit
Knowing the Threat

Fri, Dec 6, 2019 6:47 PM
SafetyTerrifying Cybercrime Figures
The internet allows us to connect with each other from all over the world, find the answer in a matter of seconds to almost every question, order food, get directions, send pictures, and so much more.